Why scammers lie: social engineering, fake charges, and why antivirus alone won’t save you
Oct 06, 2025“It’s much less work for scammers to tell you you’ve been hacked than to actually hack you.” — As a certified ethical hacker I tell clients this all the time. Scammers want one thing: to create panic so you take an action that hands them money, access, or credentials. This post explains why they lie, what “social engineering” means, why antivirus programs can’t protect you from being conned, and the exact next steps to stay safe.
Scammers rely on fear, urgency, and authority — not technical complexity.
Social engineering = tricking people into doing something (clicking, calling, giving a password).
Antivirus detects malware, not lies. If you follow instructions a scammer gives (install remote-access, call a number, or enter credentials), an AV product can’t stop you from handing over access.
When in doubt: stop, screenshot, and close. Don’t call numbers or install software from a popup or unknown caller.
What is social engineering?
Definition: Social engineering is the art of manipulating people into performing actions or divulging confidential information.
Common levers used: urgency (“act now”), authority (“I’m from Microsoft/Bank”), scarcity (“limited time”), fear (“your account will be deleted”), and helpfulness (“I’ll fix this for you”).
Goal for scammers: get you to do something they can profit from — pay, give credentials, or install remote control tools.
Why antivirus can’t stop social engineering
Antivirus = technical defense: it looks for malicious files, suspicious processes, and dangerous websites.
Social engineering is human-first: a convincing phone call or a believable-looking popup asks you to approve the action. If you approve it, you bypass technical checks — AV can’t block a user from entering their own password or dialing a scammer.
Example: a popup tells you to call a number to “remove viruses.” You call and the scammer guides you to install remote-access and then has you approve access. That’s not a malware detection failure — that’s a user-driven compromise.
Common Scams
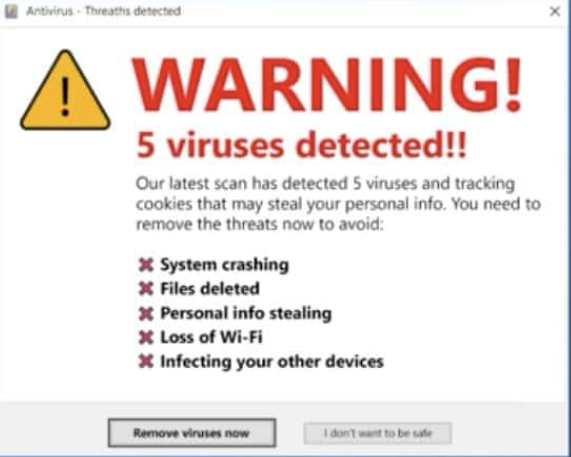
Example A — “You’ve been hacked! Call now” (web/browser popup)
“WARNING: Your computer has been hacked. Call 1-800-xxxxxx immediately to recover your files.”
Why this is a scam
It uses urgent, fear-based language and provides a phone number to call (instead of showing a legitimate vendor UI).
Legit software vendors don’t give a random phone number in a popup to call for immediate help.
What’s really happening
The popup is usually delivered by a malicious ad (a “poisoned” ad) or by a compromised site. The popup’s goal is to get you to call; once you call, the “support” agent asks you to install remote-access or pay for a fake “cleanup” service.
What to do next
Don’t call the number.
Take a screenshot (for reporting / teaching).
Close the tab or browser (Force Quit / Task Manager if needed).
Run your installed antivirus or Malwarebytes from your programs menu (not from the popup).
If you called and gave access, immediately disconnect the machine from the network and contact a trusted technician.
Example B — “Unauthorized charge — click to dispute” (fake payment alert)
“We detected a $399 charge on your card. Click here to reverse the transaction.”
Why this is a scam
Pressure to click a link and enter payment or login credentials. The message often looks like your bank but comes from an odd sender or domain.
What’s really happening
The link leads to a credential-harvesting site or a fake payment page that captures card details. If you enter credentials, the attacker can reuse them elsewhere.
What to do next
Don’t click the link.
Log into your bank or card provider directly (don’t use links).
Check recent transactions from the official app/site.
If a charge is real and you don’t recognize it, call your bank using the number on the back of your card.
Example C — “We found malware — install this cleaner now” (download prompt)
“Download our scanner to remove 24 infections now.”
Why this is a scam
The offered “cleaner” is usually malicious or a paid fake product. Prompts to download and run unknown executables are unsafe.
What’s really happening
The “scanner” is often adware or remote-access malware. Running it gives the attacker code execution or a maintenance path to later abuse.
What to do next
Don’t download or run unknown tools.
Use your installed antivirus or reputable scanners (Windows Defender, Malwarebytes) that you downloaded from the vendor’s site.
If you’ve already installed something, run full scans and consider a restore point or reinstall.
Example D — “We need to verify your account — enter code” (phone/social engineering)
You receive a call saying they’re from “your email provider,” asking you to read a two-factor code that was just sent to you.
Why this is a scam
The scammer triggers a real two-factor code (via a login attempt) and then social-engineers you into reading it, which hands them access.
What’s really happening
They try to log in and the 2FA code is sent to you; by getting you to recite it or paste it, they finish the login.
What to do next
Never read a 2FA code to a caller.
Tell them you did not request that and hang up.
Change your password from a secure device and revoke active sessions.
Short FAQ (common quick answers)
Q: If my antivirus says “no threats,” does that mean I’m safe?
A: It means no known malicious files were found — but it doesn’t mean a scammer can’t trick you into installing something or giving away credentials.
Q: What if I did call and gave remote access?
A: Disconnect the PC from the internet, uninstall the remote-access program, change passwords from a clean device, and contact your bank if you shared payment info. Consider a professional forensic check if sensitive data was exposed.
Q: Are Macs immune?
A: No. Macs are targeted with browser popups and social engineering; the tactics differ but the human element is the same.
Remember:
If you get a scary popup or an urgent-sounding call:
Have a PCRescue Subscription?
You already have access to free tools and support
If you don't have a PCRescue Subscription, try one free for 30 days.
No credit card required.
Stay connected with news and updates!
Join our mailing list to receive the latest news and updates from our team.
Don't worry, your information will not be shared.
We hate SPAM. We will never sell your information, for any reason.